MAC-Based Access Control
- Cisco Wireless Authentication Protocol
- Cisco Ise Wireless Authentication Settings
- Cisco Ise Wireless Mab Authentication
PermitAccess tells ISE to send an ACCESSACCEPT response. You can see how it’s configured by doing the following: Navigate to the Cisco ISE page we had opened for the Authentication Policy and click Conditions on the left side; Click Authorization and then Compound Conditions; Under Name, click Wireless802.1X. Configure Wireless Dot1x Authentication Cisco ISE and Cisco WLC #trainingtechlabs #arnelpabustan@hotmail.com.
Cisco Wireless Authentication Protocol
It is critical to control which devices can access the Wireless LAN. MAC-Based Access Control can be used to provide network access control on MR series access points. With MAC-Based Access Control, devices must be authenticated by a RADIUS server before network access is granted on an SSID.
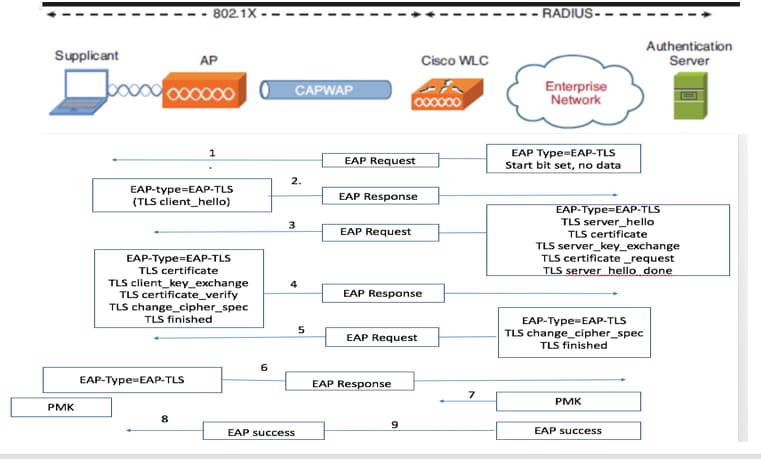
The Access Point (Authenticator) sends a RADIUS Access-Request to the RADIUS server containing the username and password of the connecting wireless device based on the association process. With MAC-based Access Control, the username and password combination is always the MAC address of the connecting device, lower case, without delimiting characters.
If a RADIUS policy exists on the server that specifies the device should be granted access and the credentials are correct, the RADIUS server will respond with an Access-Accept message. Upon receiving this message, the AP will grant network access to the device on the SSID.
If the RADIUS server replies with an Access-Reject, the device does not match an existing policy or the RADIUS server has a rule denying the client and the AP will not grant network access to the device.
Below is a diagram showing a successful authentication exchange:
Security Considerations
MAC-Based Access Control has some security implications which must be considered before using this method as a primary method to secure a wireless network.
- It is not an association method that supports wireless encryption. Communication between wireless clients and the MR is not encrypted and can be intercepted and viewed as clear text by “man-in-the-middle” devices using easily accessible wireless capture tools. Therefore clients will need to rely on upper layer protocols for encrypting traffic, such as SSL or IPsec, once a device has gained network access.
- Because the MAC address of the device is used as the authentication credentials, an attacker can easily gain network access by spoofing the MAC address of previously authenticated clients.
Cisco Identity Services Engine may be used for device posturing when paired with Meraki Access Points. Cisco ISE is another option for posturing devices enabling many additional business use cases.
The Meraki APs will pass necessary information over to Cisco ISE using 802.1x RADIUS and honor a URL redirect that is received from the Cisco ISE Server. Using CoA the Cisco ISE server can instruct the device to reauthenticate if authentication status changes after the device posturing is complete.
This posturing mechanism allows devices to be placed on a secure provisioning vlan while they are postured. After the posturing is complete, the device can be reauthenticated and placed on the corporate network upon being profiled.
Configuration
The following sections of this guide will outline a configuration example with using Cisco ISE as the posturing system which is also hosting the Captive portal for posturing.
Meraki Access Point Dashboard Configuration
The Meraki Access Point configuration is outlined below all on the Access Control Page for a particular SSID (Wireless > Configure > Access Control).
Configure WPA2-Enterprise Authentication
Select WPA2-Enterprise Authentication from the association requirements section of the access control page.
Enter the details for the RADIUS server including the IP address, port, and secret. If using dynamic group policies select Airspace-ACL-Name for the RADIUS attribute specifying group policy name.
Configure CWA for Splash page
Select Cisco Identity Services Engine (ISE) Captive Portal Authentication in the Splash Page section of the access control page. This setting will honor the cisco custom url-redirect attribute sent from Cisco ISE.
If the option to configure ISE is not available, please contact Meraki Support to have the feature enabled.
Configure the Walled Garden
The IP address of the Cisco ISE server needs to be added to the walled garden to ensure that a client will be permitted through the walled garden before being authenticated by the Cisco ISE server.
DNS traffic is permitted by default through the walled garden
Disable CNA
As of Cisco ISE 2.2, Apple CNA is supported for Guest and BYOD. Beginning July 26th, 2017, Apple CNA and Android captive portal detection are enabled by default on Cisco Meraki MR access points. On iOS 7+ and OS X, the client will automatically launch a mini-browser (CNA) that takes the user to the splash page to complete authentication and gain access to the network. Android devices will display a notification on the device prompting the user to sign into the Wi-Fi network. Tapping the notification will launch the device browser and direct the user to the splash page. To disable CNA and captive portal detection, append the following 17.0.0.0/8 IP range and domain names to the walled garden as shown below:
Disabling CNA will require that users manually open their web browser before being presented with the splash page. Applications on the user's device that require Internet connectivity will not function as expected until the user has opened their web browser and completed authentication via the splash page.
Cisco ISE Configuration
The following sections focuses on Cisco ISE 1.3. Configuration may vary based on the version of Cisco ISE.
Create the Internal Identity Users
Cisco Ise Wireless Authentication Settings
Navigate to Administration > Identity Managment > Identities, and click on the users folder. Create two new users (employee & contractor) using the Add button.
New user Screen
User list after both users have been added
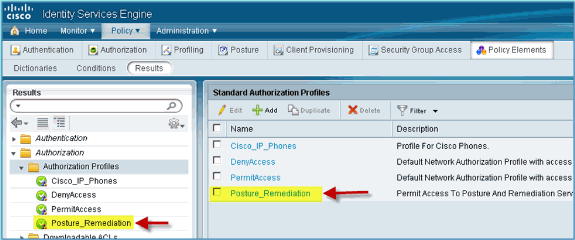
Create the Authorization Profilies

On the ISE, the authorization profile must be created. Then, the authentication and authorization policies are configured. The individual Meraki APs should already be configured as a network devices.
Posture Asessment Authorization Profile
- Select the ACCESS_ACCEPT option for Access Type
- Check the Web Redirection check box, and choose Client Provisioning (Posture) from the drop-down list.
- Choose the name of provisioning portal you would like to posture users with. (This example is using Client Provisioning Portal (default) which is a built in portal)
- Enter a ACL name (This does not map to anything on the Meraki Dashboard)
- A custom IP address or host name can be defined that points to the Cisco ISE server. If left unchecked ISE will use the hostname and domain name defined during the system setup
Contractor / Employee Access Authorization Profile
- Select the ACCESS_ACCEPT option for Access Type
- Check the optional Airspace ACL Name check box, and define the name of a custom group policy configured on the Meraki Dashboard. This example uses employee-group for the ACL in the Employee_Access Authorization Profile and contractor_group for the ACL in the Contractor_Access Authorization Profile.
Create a Authentication Rule

Cisco Ise Wireless Mab Authentication
Ensure that the ISE accepts all of the 802.1X authentication from the Meraki AP and make sure it will drop authentication even if the user is not found.
Under the Policy menu, click Authentication.
The next image shows an example of how to configure the authentication policy rule. In this example, a rule is configured that triggers when 802.1X is detected.
Enable Profiling Probes
The ISE needs to be configured as probes to effectively profile endpoints. By default, these options are disabled. This section shows how to configure ISE to be probes.

From the Edit Node page, select the Profiling Configuration and configure the following:
DHCP: Enabled, All (or default)
DHCPSPAN: Enabled, All (or default)
HTTP: Enabled, All (or default)
RADIUS: Enabled, N/A
DNS: Enabled, N/A
Enable ISE Profile Policy for Devices
Out of the box, ISE provides a library of various endpoint profiles. Complete these steps in order to enable profiles for devices:
For this example we are enabling Identity Group Creation for the following profiles:
OSX-Workstation
Apple-iPod
Apple-iPad
Apple-iPhone
The screenshot below shows how to enable the Identity Group creation for OS X Workstations
Create Authorization Policies
In order to verify the authorization rules, navigate to Policy > Authorization.
Users who associate to the SSID may have been profiled and match one of the defined profiled device types will either use the Employee_Access or Contractor_Access authorization profiles based on the Internal User that is loggin in via 802.1X.
Users who associate to the SSID may not have been profiled yet. This is why they match the third rule, which uses the Posture_Remediation authorization profile to redirect them to the Posture Portal.
Add Meraki APs to Cisco ISE
Add the Meraki AP management IPs or subnet as a Network Access Device from Administration > Network Resources > Network Devices.
